See a Demo
You're just one step away from seeing Call Loop in action.
Enter your information below to watch a demo right now.

Yes, text messages can absolutely be used in court, but they don't just waltz in as evidence on their own. Think of it this way: a text message is like a mysterious note found at a crime scene. Before the jury can even look at it, you have to prove who wrote it and why it matters.
The role of text messages in the courtroom has exploded over the last decade. It used to be a novel idea, but now it's just another Tuesday. With roughly 23 billion text messages flying around the globe every single day, it’s no surprise that courts have had to get savvy about treating our primary form of communication as serious evidence. You can get more insights on how the legal system is adapting at leb-law.com.
But here’s the catch: just because a message exists doesn't mean a judge will let it in. Every single text, SMS log, or even a record of a ringless voicemail (also called a voicemail drop) has to clear two massive legal hurdles before it ever sees the light of day in a courtroom.
To get any digital message admitted, you have to successfully navigate two fundamental rules of evidence. Get these wrong, and your smoking-gun text is worthless.
Let’s take a look at the two main gatekeepers that determine whether a text message makes it into evidence or gets tossed out.
This table breaks down the primary legal requirements text messages must meet to be considered admissible evidence in a court of law.
These two challenges—authentication and hearsay—are where most attempts to use text messages as evidence fail. But don't worry.
This guide is your complete roadmap. We'll start with the fundamentals of authentication, then dive into how to overcome hearsay objections, and finish with practical, real-world steps for preserving your digital evidence for both civil and criminal cases.
By the end, you'll understand exactly how a simple text message can transform into powerful, case-winning evidence.
So you have a text message that could make or break your case. Before you can show it to a judge or jury, you have to get past a critical step: authentication.
Think of it like proving a handwritten signature on a contract is real. You have to show the message is genuine and hasn't been tampered with. A simple screenshot of a text conversation often won’t cut it, because anyone with a basic photo editor can alter an image.
Authentication is easily the biggest hurdle to getting texts admitted as evidence. In fact, judicial analyses show that roughly 72% of appellate cases dealing with electronic evidence run into arguments over authenticity. To get a text authenticated, you need more than just the words on the screen; you need proof of who sent it, who received it, when it happened, and that the message is exactly as it was originally written.
Courts have a few trusted methods for verifying that a text message is legit. Combining these tactics builds the strongest case for getting your evidence admitted.
It’s a classic courtroom scene: one side shows a screenshot, and the other immediately claims it’s fake. Without metadata or a witness to back it up, a judge might throw it out. This is why relying on a simple picture is so risky.
Metadata is the unsung hero of digital evidence. A screenshot shows you what was said, but the metadata proves how, when, and by whom. Those timestamps, device IDs, and phone numbers are the crucial pieces of the puzzle that confirm a message’s journey.
This is especially critical for businesses using SMS or ringless voicemail for customer communication. Keeping clean, detailed digital logs isn’t just good practice; it's a legal safeguard.
Robust reporting tools can create a clear, auditable trail of every message sent, voicemail dropped, and received, which is priceless when you need to prove a message is authentic. For any business that relies on texting, looking into platforms with comprehensive reporting and analytics features is a smart, proactive move.
While every communication platform is a little different, the fundamental need to prove a message's integrity never changes. You can get a sense of the broader principles by looking at these email authentication best practices. By holding your text evidence to these same high standards, you build a case on solid ground.
The hearsay rule is one of the most misunderstood concepts in law, but the idea is simple: you can't use out-of-court statements to prove the truth of what they're saying. Think of it as the court's way of shutting down the "he said, she said" game.
This rule throws a major wrench in things when it comes to text messages. After all, a text is, by its very nature, a statement made outside of the courtroom.
So, even if you have a smoking-gun text message or a pristine log from a ringless voicemail provider, you can't just hand it to the judge. It's considered hearsay, and without a valid legal reason, it stays out.
But this is where it gets interesting. The law is filled with exceptions to this rule—think of them as keys that unlock the courtroom door for your evidence. If you can find the right key for your text message, it gets in.
Let's break down the most common exceptions you'll use to get your text messages admitted.
Each of these provides a clear path to getting your evidence in front of the judge and jury. Let's see how they work in the real world.
The party-opponent rule is incredibly powerful. Imagine a manager sends a text saying, "Yeah, I know we violated the safety policy, just get it done." That text can be used against the company to prove they knew about the violation. The manager’s own words become the proof.
State-of-mind texts are more about capturing a moment. A message like, "I'm scared and overwhelmed by his threats" can be crucial in a harassment case to show the victim's genuine emotional distress at that time.
And finally, business records are your best friend for anything automated. A timestamped delivery report from a platform like Call Loop showing a ringless voicemail was delivered isn't just a claim—it's a routine business record that can often sail right past a hearsay objection.
“An out-of-court statement is just gossip until you can find a home for it in the rulebook. These exceptions give your text messages a home.”
In a tense contract dispute, a plaintiff’s lawyer introduced a supplier’s text that read, "We're going to be late on the shipment, I don't care what the contract says." Because it was the supplier's own statement used against them, the judge admitted it under the party-opponent exception. The jury got to see the supplier's true intentions in their own words.
A personal injury case turned when the defendant's texts from right after the accident were admitted. Messages like "I'm so sorry, I totally panicked" were allowed in to show the driver's state of mind, which helped paint a clearer picture of the event.
One of our own retail clients successfully used their ringless voicemail drop log as a business record. Because the system automatically timestamped every delivery and preserved all the metadata, the court accepted it without issue.
Getting past a hearsay objection isn't just about what you do in the courtroom; it starts way before you ever file a lawsuit.
Here are the practical steps you need to take:
By thinking strategically and aligning your evidence with the right legal exception, you can turn what looks like simple chatter into undeniable proof. Next, we'll cover the crucial steps for preserving your digital evidence so it stands up to any challenge.
Once you've zeroed in on the text messages, SMS logs, or even voicemails that could make or break your case, your next job is to preserve them perfectly. You have to think like a crime scene investigator bagging up evidence—every single step has to be deliberate to prevent what the legal world calls spoliation, or the destruction of evidence.
It all starts with a simple rule: do not delete anything. It doesn't matter if a message looks bad for you; intentionally deleting it can land you in hot water with the court, leading to serious penalties. The next move is to immediately secure the device itself and document every detail about its condition and who has handled it.
Snapping a screenshot is everyone’s first instinct, but legally, it's often the weakest move you can make. A screenshot is just a picture. It can be altered, cropped, and, most importantly, it’s stripped of its most critical component: metadata. Without the data underneath—like the exact timestamps, sender details, and network info—it boils down to your word against theirs.
Courts are getting smarter and more skeptical of screenshots because they're just too easy to fake. If you really want to prove your case, you need to go deeper and capture the entire digital footprint of the conversation. You need a verifiable, exact copy of the device's data.
Professional forensic tools are the gold standard. These specialized software applications create a bit-for-bit image of a device’s storage, capturing not only the messages you can see but also deleted data and all associated metadata, preserving it in a way that is verifiable in court.
This process establishes a clean chain of custody, proving that the evidence hasn't been touched or tampered with from the moment it was collected.
The infographic below gives you a clear picture of how a text message navigates the legal hurdles, overcoming a hearsay objection to become admissible in court.
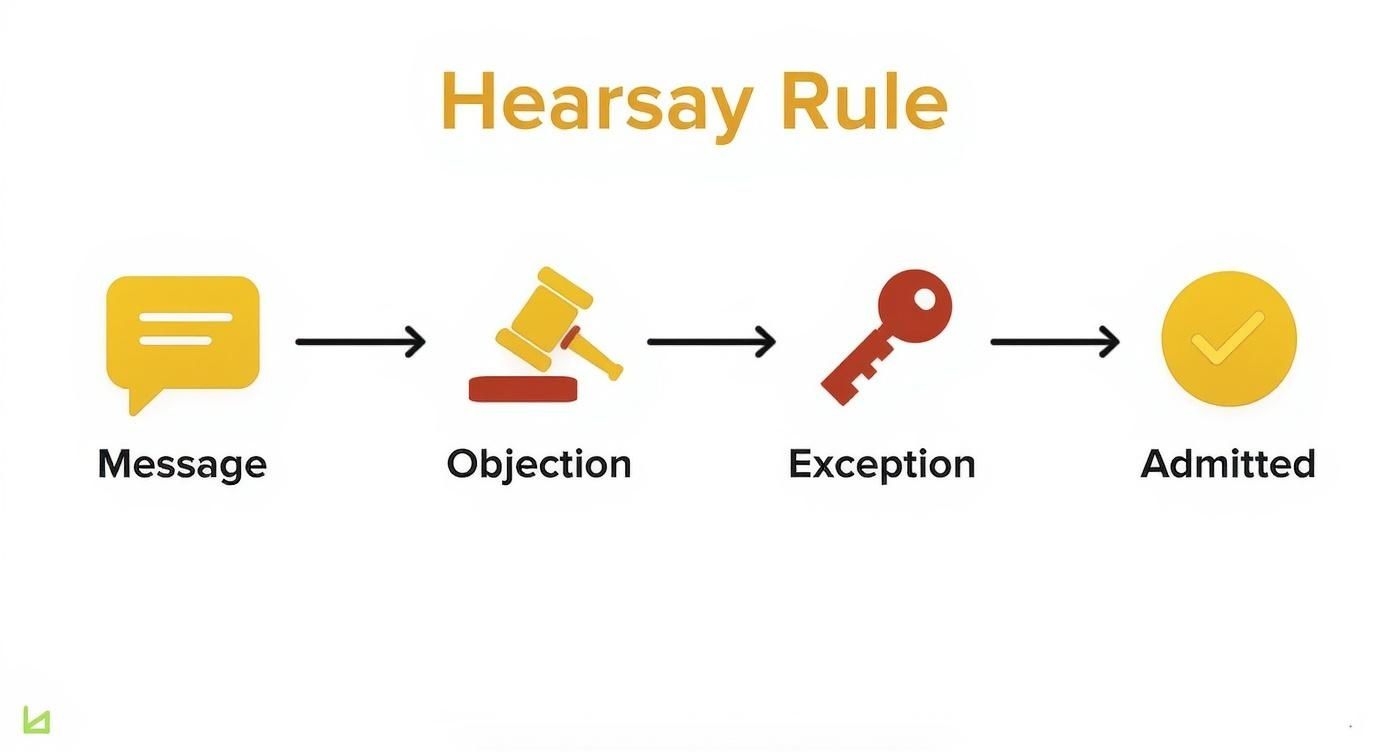
As you can see, even when a message faces an objection, it can still get in if it qualifies for one of the legal exceptions.
Getting the preservation part right is everything. For businesses, this isn't a one-off task; it should be part of a clear, documented process. Having solid practical data retention policy examples in place is a game-changer, ensuring that digital communications are stored correctly and are ready for legal scrutiny if needed.
Here are the key steps to lock down your evidence:
The legal theory behind admitting evidence is one thing; seeing it in action is another. How a text message gets used depends entirely on the type of case. The same message can mean wildly different things in a criminal trial versus a family court hearing.
In criminal law, texts often become the star witnesses. Messages showing someone planning a crime, coordinating with others, or admitting what they did can be devastatingly effective for prosecutors.
Even a text sent as a "joke" can be twisted and presented as a direct admission of guilt, showing the sender's state of mind or intent. In fact, messages proving conspiracy or coordination show up in an estimated 65-75% of organized crime cases in major U.S. jurisdictions. You can discover more insights about the role of text messages in court proceedings to see just how common this is.
The impact of text messages is just as huge in civil lawsuits, especially in the emotionally charged world of family court.
In divorce proceedings, text messages create a clear, timestamped record of behavior that might otherwise dissolve into a "he said, she said" argument. They are constantly used to document things like:
For businesses, text message records are absolutely vital. A simple SMS exchange confirming a price or delivery date can be the key piece of evidence needed to prove a verbal agreement existed, locking in the terms of a contract or showing a breach. In the same way, logs from a ringless voicemail service can be used to show that a business made a good-faith effort to contact a client as promised.
A text message captures a moment in time with candid honesty. In court, that raw, unfiltered communication can be more powerful than hours of testimony.
In personal injury lawsuits, text messages can definitively nail down negligence. The classic example is a distracted driving case. A text sent just moments before a car crash is some of the most compelling proof you can find that the driver wasn't paying attention.
Imagine this: a plaintiff's attorney presents phone records showing the defendant sent a text at 2:15 PM. Then, they play the 911 call reporting the collision, which came in at 2:16 PM. That tight, one-minute timeline creates a powerful and often irrefutable story for the jury, directly linking the driver's actions to the harm they caused. It solidifies the claim of negligence in a way that’s very hard to argue against.
It's one thing to scramble for evidence after a problem arises, but it's a whole lot smarter—and cheaper—to get your house in order beforehand. If your organization relies on SMS, messaging apps, or ringless voicemail, you absolutely need a proactive game plan.
Putting a rock-solid digital communication policy in place is the single best move you can make. It can prevent costly legal fights down the road and ensure your messages are actually usable in court if you ever need them.
This all starts with laying down clear ground rules for when and how employees can use text messaging for business. Ambiguity is your worst enemy here. Your policy needs to be explicit about what’s okay and what’s not, covering everything from professional tone to data security. The big idea is to build a culture where every single message is treated as an official business record.
A truly comprehensive policy isn't just a document—it's a system. It should include clear procedures for automatically archiving all business communications. Trusting employees to save their own texts is a recipe for disaster. You need to implement technology that automates this, capturing every message, voicemail drop, and its metadata without anyone having to lift a finger.
Regular training is just as important. Your team needs to understand the company's rules, but they also need to grasp the legal landscape they're operating in, especially TCPA regulations for any unsolicited messages. For a deeper look at staying on the right side of the law, our guide on a business’s anti-spam policy is a must-read for any organization doing outreach.
A well-defined communication strategy does more than just prepare you for litigation; it actively prevents it by promoting clarity, accountability, and compliance across your entire organization.
Want to make sure your texts will hold up under legal scrutiny? Follow this simple checklist:
Figuring out the rules of evidence can feel like learning a new language, but a few key ideas can clear things up. Here are some straightforward answers to the questions we hear most often.
Yes, in many cases, they are. When you hit "delete" on a text, the data doesn't just vanish into thin air. It usually sticks around on your device or the carrier's servers until new data overwrites it.
Think of it like a file in a filing cabinet. Deleting it is like throwing away the label, but the file itself is still in the drawer until you stuff something else in its place. Forensic experts often have the tools to go in and pull that "deleted" file right back out. If they succeed, those recovered messages face the same rules for authentication and hearsay as any other text.
One word of caution: if you intentionally delete messages you know are relevant to a legal case, you're wading into dangerous water. That's called spoliation of evidence, and courts can issue some pretty severe penalties for it.
This is a big one. A screenshot is just a picture of your phone's screen. Because it’s an image file, it’s shockingly easy to edit, crop, or completely fabricate. As you can imagine, judges are getting more and more wary of accepting them as solid proof.
A forensic copy, on the other hand, is the real deal. It’s an exact, bit-for-bit duplicate of a device's data, created with specialized software. It doesn’t just capture the words in the message; it grabs all the metadata attached to it—things like timestamps, sender information, and even location data. This process preserves the chain of custody, making the evidence far more credible and much harder to challenge in court.
A forensic copy tells the whole story of a message—who sent it, when, and from where. A screenshot just shows a picture of the words, which is why it’s so much easier to dispute.
Absolutely. Messages from any platform—whether it's WhatsApp, Facebook Messenger, Instagram DMs, or even a workplace tool like Slack—are treated the same as standard SMS texts in the eyes of the law.
They all have to clear the same hurdles to be admitted into evidence. The conversation must be relevant to the case, you have to prove who actually sent the messages (authentication), and it has to get past any hearsay objections. The tech you use to preserve and authenticate them might change a bit from app to app, but the core legal principles don't.
For businesses that need a reliable way to manage and archive their communications, Call Loop offers a powerful multi-channel messaging platform. Automate your outreach across SMS, voice, and ringless voicemail with a system designed for compliance and scalability. Learn how Call Loop can secure your business communications today.
Trusted by over 45,000 people, organizations, and businesses like