See a Demo
You're just one step away from seeing Call Loop in action.
Enter your information below to watch a demo right now.

Yes, text messages can absolutely hold up in court. But it’s not as simple as just showing the judge your phone. For a text to be treated as valid evidence, it has to jump through some serious legal hoops to prove it’s authentic, relevant, and reliable.
We live in an age where entire business deals and personal disputes play out in our messaging apps. This makes the question "can text messages hold up in court?" more critical than ever. Texts are now a go-to form of evidence, but getting them admitted requires clearing some major hurdles. A simple screenshot might look damning, but courts demand a lot more to feel confident the evidence is trustworthy and hasn't been doctored.

This is a huge deal for businesses. Think about it: an SMS confirming new contract terms, a ringless voicemail with a critical update, or an MMS showing a product defect. Any of these can become the smoking gun in a legal battle. Understanding the rules of evidence isn't just for lawyers anymore; it's vital for anyone using digital messaging to run their business.
The legal world has had to play catch-up with technology, and it wasn't always a smooth ride. The good news is that the admissibility of text messages has soared. Today, texts are accepted in 90% of U.S. courts thanks to updates to the Federal Rules of Evidence in 2017.
It wasn't always this way. Before 2012, only about 28% of digital evidence like texts made it past the judge, mostly due to tough authentication rules. Thankfully, a series of landmark cases have made it easier to use circumstantial evidence to prove a text is the real deal. You can find more insights on how these standards have changed on magnals.com.
At its core, the court needs to be certain of three things: who sent the message, that the message hasn't been changed, and that it's relevant to the case. This is why official records are always better than a simple screenshot.
For a text to make it into evidence, it generally has to tick these boxes:
To help you keep track, here's a quick rundown of what courts are looking for.
This table breaks down the core requirements for a text message to be considered valid evidence in a court of law. Getting these details right can be the difference between a key piece of evidence being admitted or thrown out.
Ultimately, the more of these factors you can satisfy, the stronger your case will be for getting those text messages admitted as evidence.
So, you want to use a text message in court? It’s not as simple as just flashing your phone screen at the judge. Before a message ever sees the light of day in a courtroom, it has to get past two major legal gatekeepers: Authentication and the Hearsay Rule.
Think of them as two locked doors. You need to unlock both before your texts can be considered credible evidence.
First up is authentication. Just like you'd need to prove a handwritten letter wasn't a clever forgery, you have to prove a text message is the real deal. A simple screenshot often won’t cut it because they’re just too easy to fake. The court needs solid proof of who sent the message and that it hasn't been tampered with.
Authentication is simply the process of proving your evidence is what you say it is. It’s about connecting that text message to a specific person and confirming its content is exactly as it was sent. Courts have a few go-to methods for this, and they usually work best when you combine them.
Here are a few common ways to get it done:
Getting this right can sometimes involve bringing in an expert to explain the technical side of things. If you want to dive deeper into the procedural requirements and rules governing expert evidence, it’s worth understanding how their testimony is handled in court.
Once you've authenticated the message, you hit the second hurdle: the hearsay rule. In simple terms, hearsay is an out-of-court statement used to prove that what it says is true. Basically, the court doesn’t like relying on "he said, she said"—it wants the person who made the statement to be in court, under oath, where they can be cross-examined.
A text message often falls squarely into the hearsay category. But don't worry, the legal system has created a bunch of exceptions, and many texts can sneak through if they fit one of them.
Key Takeaway: A statement isn't considered hearsay if you're using it for a different reason—like showing the effect it had on the person who read it, or proving the sender's state of mind.
For example, a threatening text might be used not to prove the threat was real, but to show that the recipient was terrified. That's a critical difference.
Here are some of the most common hearsay exceptions that apply to text messages:
But even with these exceptions, building a case solely on texts is a shaky strategy. It's a striking fact that courts demand corroborating evidence in 85% of criminal cases globally where texts are used. One law firm's analysis found that only 22% of U.S. felony trials relying mainly on texts led to a conviction without other proof. The hearsay rule makes it even tougher; in some states, as many as 60% of text message submissions get challenged as hearsay.
Once a text message makes it past the initial legal hurdles, the real inspection begins. Think of it like a digital crime scene investigation. A court needs to look beyond the words on the screen and dig into the underlying data to make sure the evidence is trustworthy and hasn't been messed with.
This is why the answer to "can text messages hold up in court?" is always "it depends." It’s not just about what was said, but about proving how, when, and by whom it was said—all while keeping a perfect, unbroken trail of evidence from the phone straight to the courtroom.
Every single text message, voice broadcast, or ringless voicemail comes with a hidden layer of information called metadata. This is the message's digital fingerprint, and it's gold when it comes to proving authenticity. Metadata isn't the message content itself; it's the data about the data.
Courts love metadata because it’s much, much harder to fake than the text of a message. It typically includes:
This information paints a rich, verifiable picture that a simple screenshot just can't provide. It’s the digital version of a postmarked envelope, telling the court exactly where the message came from and when it was sent. That level of detail makes the evidence far more convincing.
The chain of custody is a critical legal concept. It's basically a chronological paper trail documenting who has handled the evidence, when they handled it, and what they did with it—from the moment it's collected until it's shown in court. A clean chain of custody proves the text message hasn't been altered or tampered with.
For digital evidence, this means using a forensically sound method to extract the messages. Simply forwarding a text or taking a screenshot breaks this chain, as the data can be easily modified in the process.
This is where professional communication platforms give you a massive advantage. They can generate official, uneditable logs that serve as a rock-solid link in the chain of custody. Understanding how this fits into the overall workplace investigation process shows just how vital these procedural steps are in any formal inquiry.
A single text message, yanked out of a longer conversation, can be incredibly misleading. Sarcasm, inside jokes, and simple clarifications get completely lost, which can change the entire meaning of a message. Courts know this and are usually very skeptical of cherry-picked texts.
For example, a message saying, "I'll make sure you pay for this," sounds like a threat on its own. But if the previous five texts were about splitting a dinner bill, the context changes everything. To avoid this kind of misinterpretation, you should always aim to present the entire conversation thread. It gives the judge or jury the full, honest picture they need to make an informed decision. The security of these threads is also a factor, as communication integrity is crucial.
Digital forgery is a very real risk, so courts are rightly cautious. Technology has made it alarmingly easy to create fake text message conversations that look completely authentic. This is the biggest reason screenshots are such weak evidence—they are the easiest format to manipulate. Official records from a phone carrier or a secure business messaging platform will always be the gold standard, providing the metadata and verifiable proof needed to stand up to tough legal scrutiny.
It's one thing to talk about legal theory, but it's another to put a practical strategy in place for your business. To make sure your SMS, MMS, and even ringless voicemail communications can hold their own in court, you have to be proactive. This means building systems that create a powerful, verifiable paper trail to shield your business from future disputes.
The best defense is a good offense. Don't wait until you're scrambling to piece together evidence after a problem blows up. The goal is to have a system that automatically preps your communications to be court-ready from day one. This not only puts you in a stronger legal position but also builds better, more compliant habits across your team.
Using personal cell phones for business messaging is a recipe for disaster. They just don't have the robust record-keeping features needed to stand up to legal scrutiny. A professional communication platform is built to solve this exact problem, giving you a centralized, secure, and verifiable system for every message you send.
Picking the right platform is everything. You need to look for features specifically designed to maintain the integrity of your communications, turning every text into a potential piece of rock-solid evidence.
Let's look at the essential features a business messaging platform should have to ensure your communications are organized, compliant, and ready for court if the need arises.
These features aren't just nice to have; they are the bedrock of a defensible communication strategy, turning every message into a verifiable business record.
This flowchart breaks down the basic steps a court takes when looking at evidence, which really drives home why having organized records is so important.
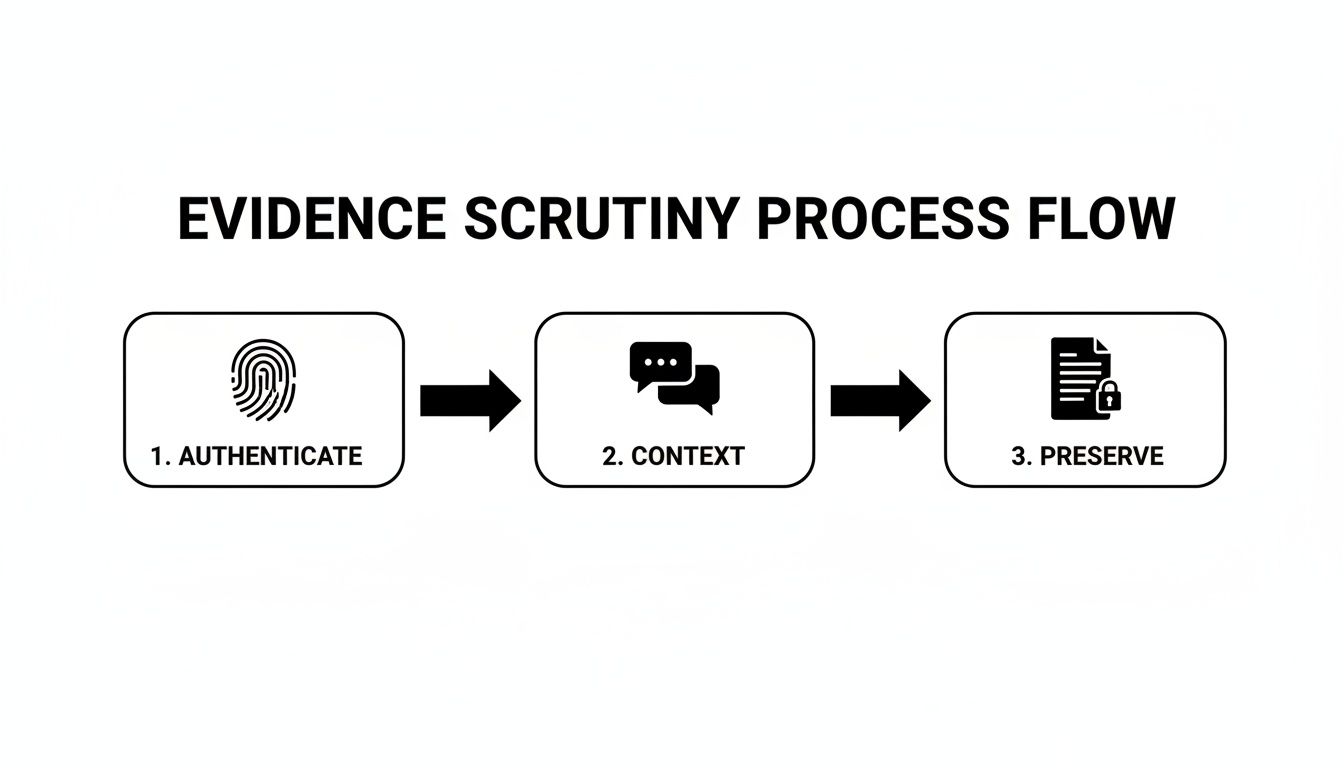
As you can see, proving a message is authentic is the first hurdle. Then you have to establish its context and show it was preserved—all things a professional platform makes way easier.
One of the most powerful things you can do to make your communications court-ready is to meticulously document user consent. A clear opt-in record not only keeps you compliant with rules like the TCPA but also proves the communication was legitimate and wanted.
Having an easily accessible record of when and how a user opted in can shut down disputes before they even begin. It establishes a clear, consensual relationship from the start.
This is non-negotiable in highly regulated industries. Take healthcare, for instance, where secure messaging is an absolute must. Using a platform that supports data privacy rules is critical for protecting patient info and defending your practices. For a closer look at this, check out our guide on HIPAA compliant texting apps to see how the right tech keeps you on the right side of the law.
Text messages are now a cornerstone of evidence in courtrooms. This is especially true in family law, but for businesses, it means that your compliant SMS campaigns—with their clear opt-ins and detailed records—can become legal gold if a dispute pops up. The National Association of Attorneys General notes that in 2023, an impressive 72% of U.S. jurisdictions now accept circumstantial evidence for texts, a huge jump from just 45% in 2012. This trend makes them more reliable than ever.
Beyond the platform, your internal processes are just as important. Get these few best practices locked in, and you'll always be prepared.
Never Delete Communications: Drill this into your team: never delete messages related to business deals or customer chats. Deleting evidence, even by accident, can be seen as "spoliation" and bring on serious legal penalties.
Preserve Full Conversations: Don't just save the "good parts." Courts want to see the whole picture, and presenting a complete conversation thread shows you're being transparent and credible. Cherry-picking messages is a massive red flag.
Train Your Team: Make sure everyone understands that their professional communications matter. Remind them that every message they send—whether it's SMS, MMS, or a voice broadcast—is a permanent business record that could end up under a microscope one day.
By pairing the right technology with smart, consistent processes, you can turn your everyday business communications into a well-organized, defensible archive. This proactive approach is the key to making sure your text messages will hold up in court if you ever need them to.
When people ask, "can text messages hold up in court," they're usually just thinking about SMS. But savvy businesses know that's just one piece of the puzzle. In reality, a smart communication strategy involves multiple channels, and things like ringless voicemail and voice broadcasting can be just as powerful—if not more so—when it comes to creating a solid evidentiary trail.
Think of it this way: relying on just one channel is like trying to tell a story with a single photo. Sure, it shows something, but it lacks context. By using a mix of texts, voice broadcasts, and ringless voicemails, you’re creating a whole photo album. Each channel leaves its own distinct footprint, giving you a much stronger, more complete picture to present if a dispute ever comes up.
Ringless voicemail is a fascinating tool. It lets you slide a message directly into someone's voicemail box without making their phone ring. It’s non-intrusive, which is a huge deal in legal contexts, especially when you're navigating the tricky waters of the Telephone Consumer Protection Act (TCPA).
The real magic, from an evidence standpoint, is in the delivery logs. A professional platform will give you a "successful drop" receipt for every single message. This isn't just a simple call log; it's a digital confirmation slip proving your message was successfully handed off to the carrier's voicemail server. It’s your proof that you communicated with someone without ever actually disturbing them with a call. To get a better handle on how this works in practice, check out this guide on ringless voicemail for business.
A "successful drop" receipt is gold. It’s a timestamped, verifiable record showing a specific message was delivered to a specific number at a specific time. This kind of documentation is exactly what you need to shut down claims of harassment or TCPA violations.
Voice broadcasting, where you send a pre-recorded audio message to a list of people, adds another powerful layer to your evidence file. The most obvious piece of proof here is the audio recording itself. A crystal-clear recording of your broadcast proves exactly what you said, word for word.
But it gets even better when you pair that audio file with the detailed call logs from your broadcasting platform. These logs can show you:
The key is to keep both the audio file and the logs together. One proves what you said, and the other proves who you said it to and when. This combination is invaluable in situations involving things like contract updates, service alerts, or public safety announcements where you absolutely must prove that specific information was shared. If you also have documented opt-in consent for these messages, you’ve built a fortress of evidence that goes way beyond what a simple text message can offer.
Knowing what not to do is just as important as knowing what you should do when preparing evidence for a legal challenge. Even with the best intentions, a few simple missteps can completely torpedo your efforts and get critical text message evidence tossed out by a judge.
If you want your communications to hold up in court, you have to steer clear of these common—and costly—pitfalls.
The biggest mistake we see people make? Relying on screenshots. They seem fast and easy, but in the eyes of the court, they're notoriously weak. Why? Because they are incredibly simple to fake.
A sharp opposing counsel will pounce on the authenticity of a screenshot, and they'd be right to. Dozens of apps exist that can generate a completely fabricated text conversation in seconds.
Think of a screenshot like a photocopy of a handwritten note. Sure, it shows the words, but it does absolutely nothing to prove who wrote it or when. This is exactly why judges are so skeptical.
To build a solid foundation for your evidence, you need official, exportable logs from your communication platform or phone carrier. These records provide the hard, verifiable data that screenshots just can't offer:
Relying on screenshots is a gamble you just don't want to take. When the authenticity of your evidence comes into question, a verifiable log is your best—and often your only—defense.
Another fatal error is deleting messages, even if you think they’re irrelevant or potentially unhelpful to your case. This act has a legal name: spoliation of evidence, and it can come with some seriously severe consequences.
If a court decides you intentionally destroyed potential evidence, it won't just hurt your case; it can get you hit with major penalties.
We're talking heavy fines, the outright dismissal of your claims, or an "adverse inference" instruction. That last one is a real killer—it’s when the judge literally tells the jury to assume that whatever you deleted would have been bad for your side.
Suddenly, that innocent inbox cleanup looks like a deliberate attempt to hide the truth. That's a perception you'll have a very hard time shaking.
Finally, never, ever present cherry-picked messages. Ripping a single text out of a long, back-and-forth conversation is a massive red flag for any judge. Context is king.
When you only show the messages that paint you in a good light while hiding the rest, your evidence immediately looks manipulative and untrustworthy.
Always be prepared to present the entire conversation thread. This transparency shows the court you have nothing to hide and gives a full, honest picture of the exchange. It builds your credibility and makes it far more likely that your digital evidence will be taken seriously.
Even when you feel like you've got the rules down, the real world has a way of throwing curveballs. Let's tackle some of the most common questions that pop up when dealing with text messages, ringless voicemail drops, and other digital communications in a legal setting. Think of these as quick, practical answers for situations you might actually run into.
You can submit screenshots, but you're walking in with some of the weakest evidence possible. They're incredibly easy to challenge in court.
Why? Because they lack the verifiable metadata—the digital breadcrumbs like precise timestamps and sender info—that a court needs to trust that they're authentic. Not to mention, it's shockingly simple to edit a screenshot.
That's why courts heavily favor evidence with a clean, provable chain of custody. Official records exported straight from a business messaging platform or phone carrier are infinitely more credible because they include all the underlying data that makes the evidence trustworthy.
Deleting texts that are tied to a current or even a potential legal case is a massive mistake. In legal terms, this is called spoliation of evidence, and it can land you in serious hot water.
If a judge finds you intentionally destroyed evidence, the penalties can be severe. We're talking significant fines or what's known as an "adverse inference" instruction. This is where the judge tells the jury they should assume the deleted messages would have hurt your case. The only safe policy is to preserve everything.
A core principle of evidence preservation is to act as if every communication could one day be scrutinized. This mindset protects you from accidental spoliation and ensures you maintain a complete and honest record.
HIPAA adds a whole other layer of complexity. While you can absolutely use patient communications as evidence, they have to be handled with extreme care, following strict privacy and security rules to protect Protected Health Information (PHI).
First off, using a HIPAA-compliant messaging platform isn't just a good idea—it's non-negotiable. This ensures that every bit of PHI is encrypted and stored securely. When it comes to a legal case, you'll need either proper patient authorization or a court order to disclose any of these messages. The secure, detailed logs from your platform will be your best friend, proving that you handled every communication compliantly and protecting you from any claims of HIPAA violations.
Ready to make your business communications court-ready? Call Loop provides the secure, compliant, and verifiable messaging platform you need. With features like comprehensive message logs, detailed delivery receipts for SMS and ringless voicemail, and secure archiving, you can build a solid evidentiary record. Protect your business and communicate with confidence.
Trusted by over 45,000 people, organizations, and businesses like